Cyber Threat Intelligence Maturity Platform
Your guide to strong Cyber Threat Intelligence"
The Cyber Threat Intelligence Maturity Elements
A strong Cyber Threat Intelligence program significantly enhances resilience against an uncertain world. Threat Analysts supported by the organisation investigate and understand the cyber threats faced by organisations, providing the organisation, in turn, with the required knowledge to support decision making. We have defined two pillars of CTI Maturity that drive a strong CTI program: the organisation, and Cyber Threat Intelligence. Furthermore, we identify 5 domains and 12 focus areas important for resilient CTI environments, represented by the figure below. A description of each domain, and the related focus areas, follows next.
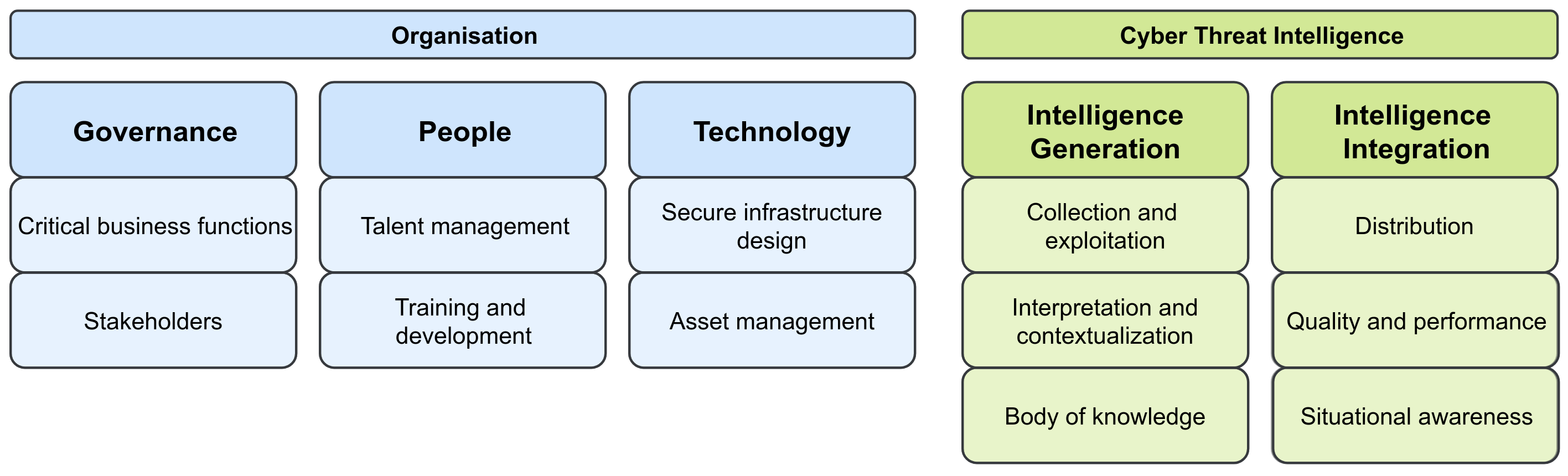
Governance
Governance provides the organizational drivers for the consumption and production of Cyber Threat Intelligence. These drivers are created through the identification of the crown jewels of the organization and are essential to a successful operation. Stakeholders identified through these crown jewels are responsible for interacting with the CTI group and the using of cyber threat intelligence products. Aforementioned processes play an essential role in the integration of CTI within organizations.
Critical business functions: Critical business functions are the elements that are essential for successful continuous operation of an organisation, having clear insight into these functions enables them to make targeted intelligence requests. These requests are used by the CTI group to create intelligence products, providing the organisation with a course of action that can be used by the organization to ensure their critical functions remain secure against cyber threats.
Stakeholder management: Stakeholders are those people and groups within an organization for which cyber threat intelligence is expected to provide value. Stakeholders use intelligence products to improve the security function of critical assets and business functions within their control. Interactively with the CTI group, stakeholders ensure the best possible intelligence products are created.
People
At the heart of every organization, you will find people, and cyber threat intelligence especially requires human expertise. Inspiring people to be their best natural selves, support their personal development to remain functional at the cutting edge, and provide security awareness for non-security personnel are essential aspects for CTI to be successful within the organization. To provide clarity for CTI talent, the objectives for the CTI group are determined and mapped into responsibilities for specific roles, which are then assigned to individuals. Finally, talents are empowered in their roles by providing them with trade-craft training and development.
Talent management: People need to know their roles and responsibilities within the organisation, and how these are connected to the objectives of the CTI group and the vision of the organization. For the CTI program to successfully meet its objectives, ample people are required with the ability to fulfil these responsibilities. Talent management considers both the distribution of roles and the sourcing of talent. Furthermore, talent management ensures the availability and readiness of CTI personnel by taking into consideration people both inside as outside the organization.
Training and development: Cyber threats are continuously evolving, along with our understanding of these threats and solutions to reduce the risk of cyber incidents. Effective cyber threat intelligence requires people that continually develop themselves. Strong education and development programs ensure that required knowledge is available within the organization and encourages continuous training opportunities. Security awareness programs assure that everyone within the organization has a basic understanding of security, how it directly affects them, and what they can do to contribute towards a more resilient environment.
Technology
To support the organisation a wide range of technologies is available, for example, computers, software, or various networked infrastructures. These technologies run the risk of being targeted by cyber actors with nefarious goals, thus providing a cyber threat to the organization. It is vital that the organisation understands their security controls, provides the means necessary for threat intelligence to improve existing controls, and give insight into all their technological assets. This enables the CTI group to provide actionable intelligence that is tailored to the organization, stakeholder, and their unique situation, giving specific advice on how to reduce cyber risk exposure.
Secure infrastructure design: Cyber resilience of an organization is accomplished through secure infrastructure design by the application of security controls. Securing an organization against cyber threats requires a range of adaptive security controls. Adaptive controls create a tight web that makes it increasingly difficult, and thus expensive, for threat actors to achieve their goals against the organization. Resilient security programs leverage cyber threat intelligence to their advantage by amplifying the effectiveness of implemented security controls.
Asset management: Organizations resilient to cyber threats know which assets are operating within their environment, which assets they expect to be present, and the state in which they operate. The CTI group relies on this knowledge to gain a greater understanding of organizational and stakeholder needs. This understanding helps them to create valuable cyber threat intelligence for their stakeholders. Furthermore, knowing which assets are active within the organizations' environment drives the discovery of vulnerabilities and weighing solutions for their mitigation.
Generation
Intelligence is both a process and a product. To create intelligence, data and information is analyzed with the objective to answers a specific request. By placing the analysis results into context to fit the need of the stakeholder, and include a course of action, intelligence is created. The creation of intelligence is a multi-process operation, requiring data collection, intelligence analysis, understanding of the stakeholders, and a body of knowledge from which information on, for example, historic events or previous intelligence products, can be drawn.
Collection and exploitation: Intelligence generation relies on the consumption of information and data collected from a set of sources. The selection of the sources happens through a set of requirements based on intelligence requirements and performance metrics. Collected information and data need processing and evaluation, to ensure reliability, believability, and consistency, before becoming useful to the analysis process.
Interpretation and contextualization: Fusing the collected data with observations, experience, and situational awareness is the first step in the analysis process. Customizing the processed information to meet the intelligence requirements and stakeholder needs will provide an organization with intelligence products. Collecting feedback from stakeholders then ensures the intended intelligence product is indeed delivered.
Body of knowledge: Cyber threat intelligence leverages a body of knowledge to create intelligence products. This corpus archives collected data created intelligence for future use, while ensuring easy and efficient access to this information for privileged users (e.g. intelligence analysts). Integration with processes within the organization ensures the CTI group has access to all the knowledge they need.
Integration
Cyber Threat Intelligence operates within and aims to influence, a larger system, thus integration into the organisation and absorption of products by stakeholders is required for it to empower the organisation. Distribution channels ensure that the correct stakeholders are reached, who are then asked to provide feedback. The feedback is used in evaluation cycles aimed to better cater to stakeholder needs. Absorption of intelligence products by stakeholders creates cyber situational awareness throughout the organization, which positively impacts the cyber resilience of the organisation.
Distribution: Stakeholders have access to their intelligence products through various distribution channels. Although initially shared with the stakeholder(s) requesting a specific intelligence product, multiple parties can benefit from the same intelligence. Thus, sharing of information processes and policies are required to ensure effective and efficient distribution.
Quality and performance: The quality of intelligence products depends on a set of product requirements and process performance. Intelligence product requirements give stakeholders a picture of what they can expect from intelligence products. Intelligence performance metrics provide insight into the functioning of the CTI program. By continuously improving the CTI processes, the expectation is that over time the quality of CTI products will improve. Furthermore, performance indicators drive the CTI process improvements and provide organizational drivers.
Situational awareness: To create effective cyber threat intelligence, the organization requires situational awareness of their cyber environment. By understanding the cyber threat landscape, CTI analysts can create the intelligence products that stakeholders use to make decisions, thus creating a resilient environment. The cyber threat landscape, however, is continuously evolving. The result is that it is paramount for organizations to observe their environment, and understand what their observations mean. Through this understanding, organizations can predict the behaviour of cyber threat actors and their impact on cybersecurity.
