Cyber Threat Intelligence Maturity Platform
Your guide to strong Cyber Threat Intelligence"
Pillars of Cyber Threat Intelligence
Cyber Threat Intelligence (CTI) can significantly improve resilience by investigating and understanding cyber threats faced by organisations. The knowledge obtained this way is then contextualized and made relevant for the organisation. The organisation, in turn, can align it’s resiliency measures and make informed decisions fostering resilience. However, CTI does not exist in a vacuum: there is an inherent tension between applying CTI and the needs and aims of the organization. A balance is required to make CTI efficient and effective Without this balance, CTI may burn valuable resources. So, a successful CTI program requires mutual support between the organisation and the CTI program. We will next unpack both sides of this argument. First, we explore CTI and how support is provided for the organisation. Second, we investigate the support needed by CTI from the organisation to operate successfully. Finally, we will merge these arguments into a holistic view of cyber threat intelligence.
Cyber Threat Intelligence:
CTI performs a supportive role, providing services and products that help the organisation to stay operational and to reduce the risks posed by cyber threats. By performing intelligence analysis, CTI converts and aligns data with stakeholders and the organisation, thus providing factual information about the current threats and how these impact the risk profile of the organisation. By continuously monitoring both the cyber threat landscape vulnerabilities within the organisation and the external threats to its (core) business processes, a CTI program provides understanding and prediction of how cyber threats may negatively influence the organisation. Continuous improvement of the cyber risk profile is stimulated through the application of intelligence products by identified stakeholders, which generates actionable recommendations to increase resilience. In these ways, CTI provides the organisation with decision-support information concerning cyber situational awareness and cyber risk reduction, supporting the mission towards a more cyber-resilient environment.
The organisation
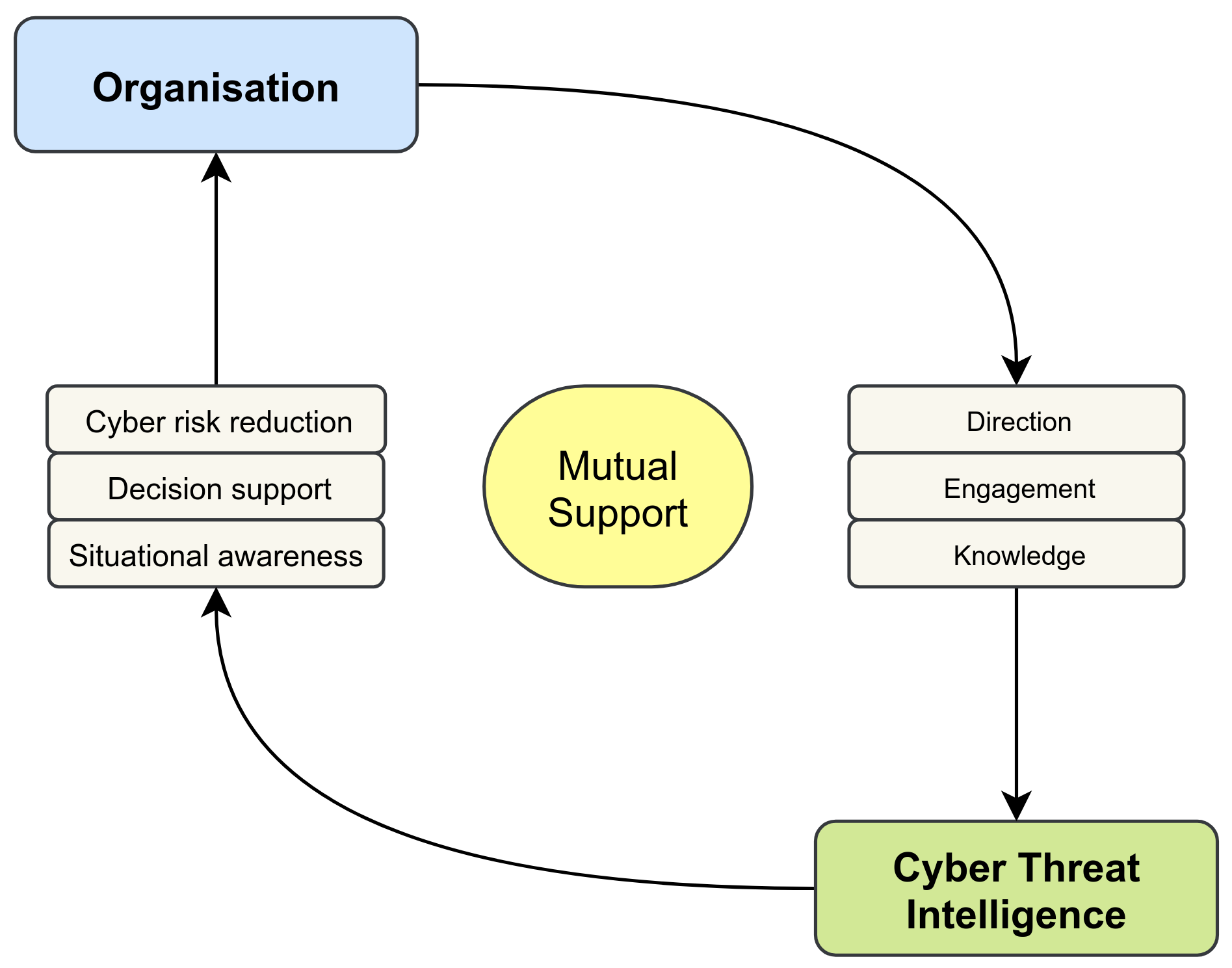
To achieve their business goals, an understanding of the critical business functions, or crown jewels, of the organisation is required. Additionally, the CTI group needs an understanding of what components and which people might be targeted by cyber threats. Such information allows relevant stakeholders to prioritize in times of duress and to successfully support risk-based decision making. Generation of CTI requires data and information, extending beyond the absorption of threat feeds. These data and information have to be processed by CTI talent, who require continuous training and development to stay current within a fast and ever-changing field. Without them, no intelligence products would be effective. The CTI-group needs an interface with the rest of the organisation. This can be organized through stakeholders who align with specific pieces of intelligence. For example, an administrator may receive new indicators to load into the firewall, or the CEO gets information of strategic importance during a merger. This requires that the stakeholders are, to a certain extent, aware of the environment in which they act. To support stakeholder interaction and build situational awareness, supporting infrastructure is required. Using these elements we create a concept map as visualised in the figure below, to be used to further drive and deepen our exploration while aligning components to nicely fit together. What we learn from these first explorations is that CTI has requirements for direction, resources and supporting functions, as well as integration and engagement.
A holistic view on CTI:
A model for CTI maturity needs to take both sides of the concept map into account, namely, CTI on the one side, and the organisation on the other. One the one side, for a CTI-program to be effective, it needs to be embedded and tightly integrated throughout the organization, i.e., CTI requires direction, knowledge and engagement from the organization. For example, without input from stakeholders on their assets and concrete information requirements, it is not possible to collect CTI that is relevant and fits the needs of the organization. Even more concretely, if the people who create CTI do not know what kind of systems, software and infrastructure is running that enable critical business processes, they cannot be on the watch for potential threats targeting these resources and processes. On the other side, threat intelligence can only be effective if it is absorbed by the organization in the right places. For instance, when a business division receives detailed information on how a threat actor can compromise critical business processes through some new type of spearfishing attack, this information must be translated into concrete actions to be useful, such as making adaptations in intrusion detection systems used, dissemination of an alert message, or awareness training for staff.
We thus propose mature CTI environments have established mutual support between the CTI-department and the rest of the organisation. This is represented by the figure above, along with the two pillars: Organisation and Cyber Threat Intelligence.
